Permissions
Connection permissions
Access rights in REWOO Scope are governed by connections. Each connection is directed and gives all users who get to the source a defined permission at the destination. There are five levels of authorization:
- None permission
- Read permission
- Write permission
- All permission
If you think of the elements as data rooms, the connections are the corridors between these rooms. However, these corridors can only be entered in one direction and determine with which powers one arrives at the other data room.
The connection between A and B contains two corridors, one from A to B and one from B to A. If one is allowed to enter A, it has no significance for the authorizations in B with which authorizations one has reached A. Only the authorization that defines the connection from A to B determines the authorization in B. This makes it possible to estimate the effects of connections without knowing the entire connection network of REWOO Scope.
If a user with read permissions encounters an element C and there is a relationship to another element D with read permissions from C to D and write permissions from D to C, the user gets read permissions on D because he gets to D via C, but he also gets write permissions on C because he gets back to C via C to D with write permissions.
Author permissions
Unlike elements, where access rights are governed by connections, types are managed by authorship. Administrators are allowed to create, read and modify all types. Therefore, they do not need any special author rights. Power users, on the other hand, may only read and modify the types they have created themselves or for which they have been assigned author rights by existing authors of that type. All other account types cannot gain access to types.
Access rights of the individual user
All users with one of the user roles Standard or Concurrent have also been assigned a start item when they log in to REWOO Scope. When the user logs in, this element is their starting point in the REWOO world. Starting from this start element, the authorization network and thus the world visible to the user is spanned via the connections.
Rulebook
None permission
- User cannot view data sheet
- Values on data sheet can be read out via formulas like OTHERASPECTS, though.
Read permission
- Read visible form
- View files
- sign (depending on configuration)
- View involved users of data sheet
- Press buttons, that are set to read
Write permission
- all of read permission
- Edit datasheet entries (if not locked)
- Edit files (if editable)
- Press buttons, that are set to write
All permission
- all from write right
- change locked fields
- view and change hidden fields
- use buttons that are set to All
- view involved users of objects and processes
- Change layout
- Change status
- Change role set
- Create subelements
- Change status of subelements
- Create connections
- Change rights of connections
Examples
Terms and preparation
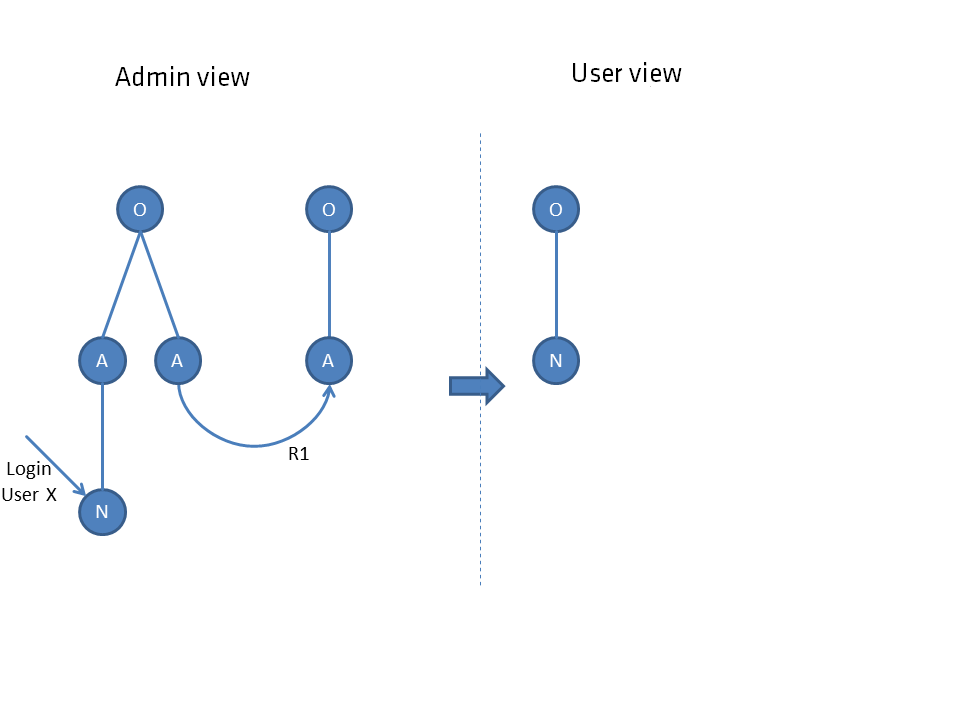
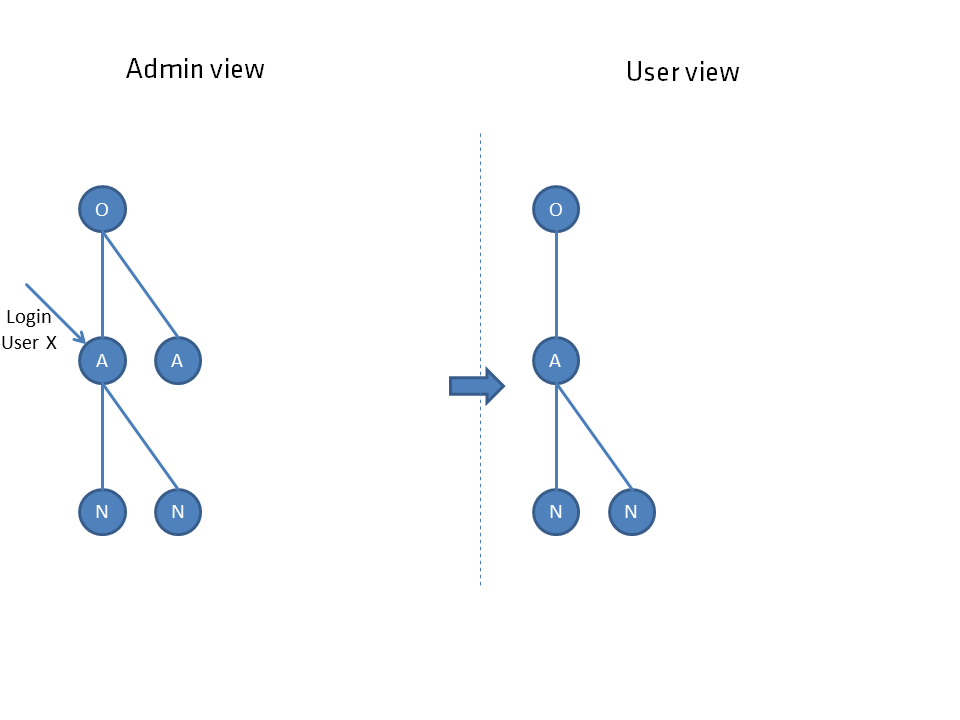
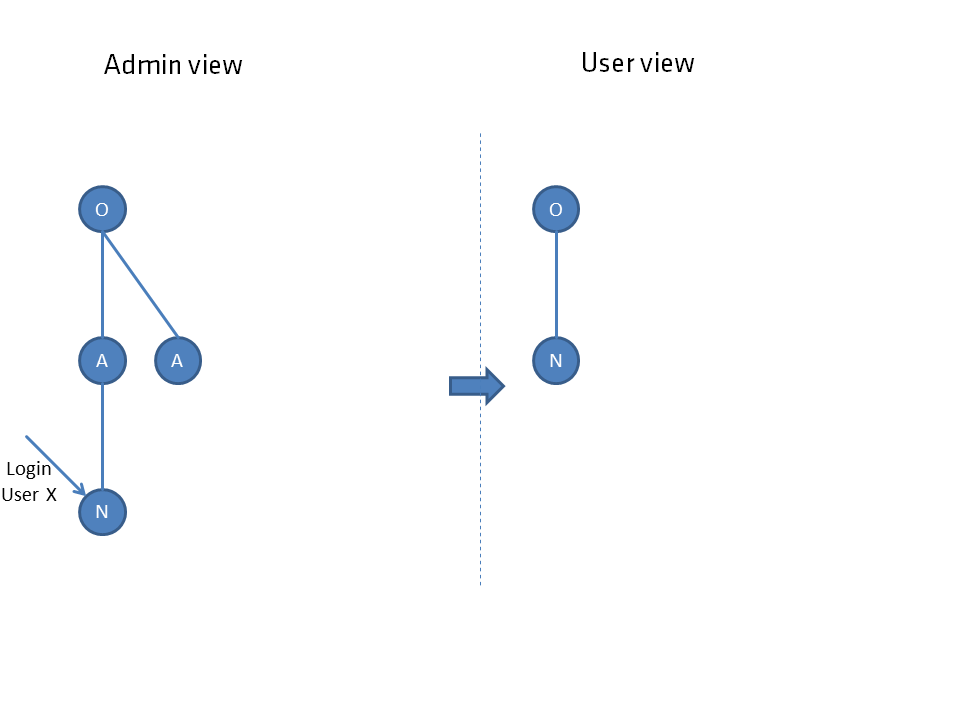
The respective image shows the situation from the administrator's view (left side) including the login element for a user. The view for the user that follows from the dependency net is shown on the right side.
The respective elements are shown as a circle, where objects O are distinguished from nodes, which are subdivided into aspects A and their child elements nodes N.
Objects are to be considered as collective elements, an aspect or a node always has a parent element and therefore cannot stand alone. The hierarchical connection is represented by straight lines. connections R are represented by curved lines. Both are used to determine the individual connection network.
For connections, an authorization that contains read or more is sufficient. A connection without permissions is to be evaluated as no connection. Since every relation contains a direction, this is to be evaluated accordingly (against one-way streets may not be navigated).
Authorization from aspect structure
When the user sees a node, he also sees the object.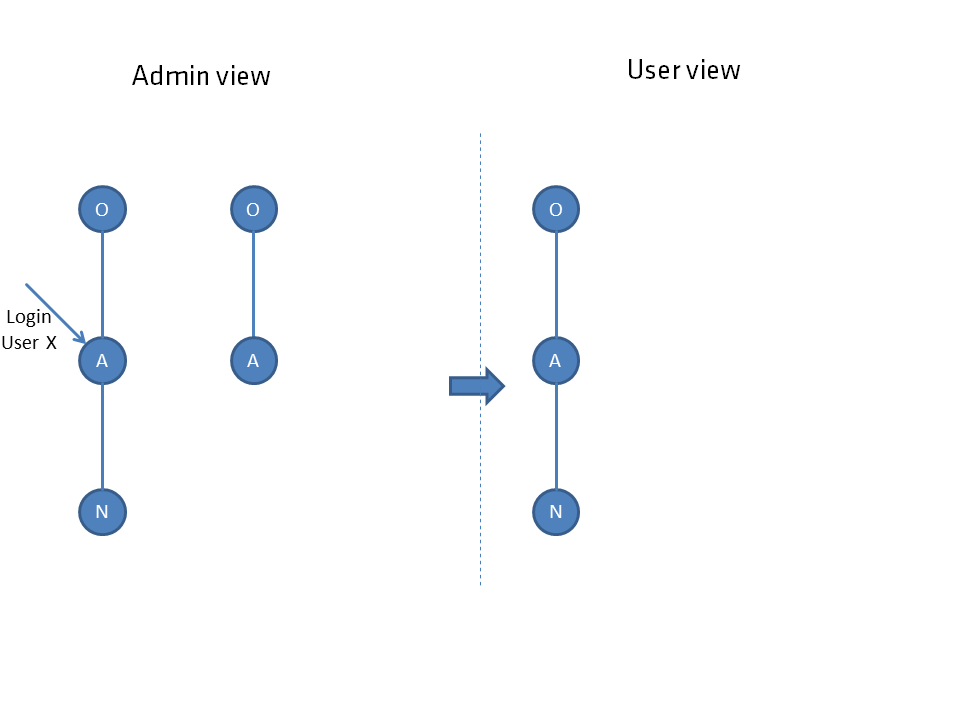 When the user sees a node of an aspect, he also sees all subnodes. Neighboring aspects remain invisible to the user.
When the user sees a node of an aspect, he also sees all subnodes. Neighboring aspects remain invisible to the user.
 The aspect is suspended for the user at the highest node he can see.
The aspect is suspended for the user at the highest node he can see.
 If there is no unique highest node, an artificial empty node is created to suspend both nodes.
If there is no unique highest node, an artificial empty node is created to suspend both nodes.
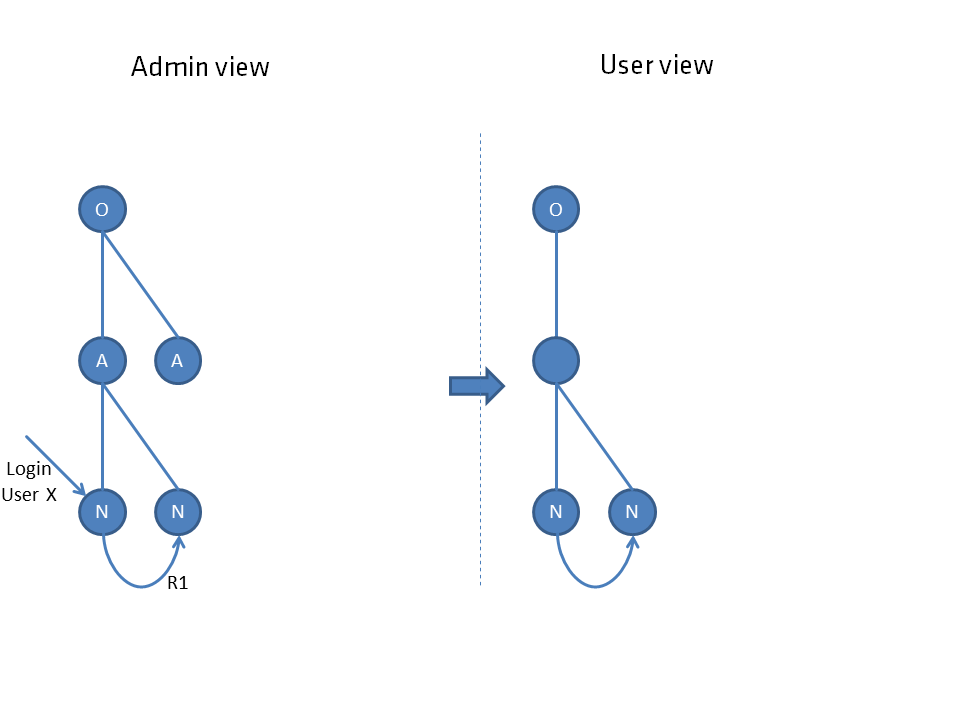
Permissions via connections
If the user can see one node, he can also see all nodes connected by connection.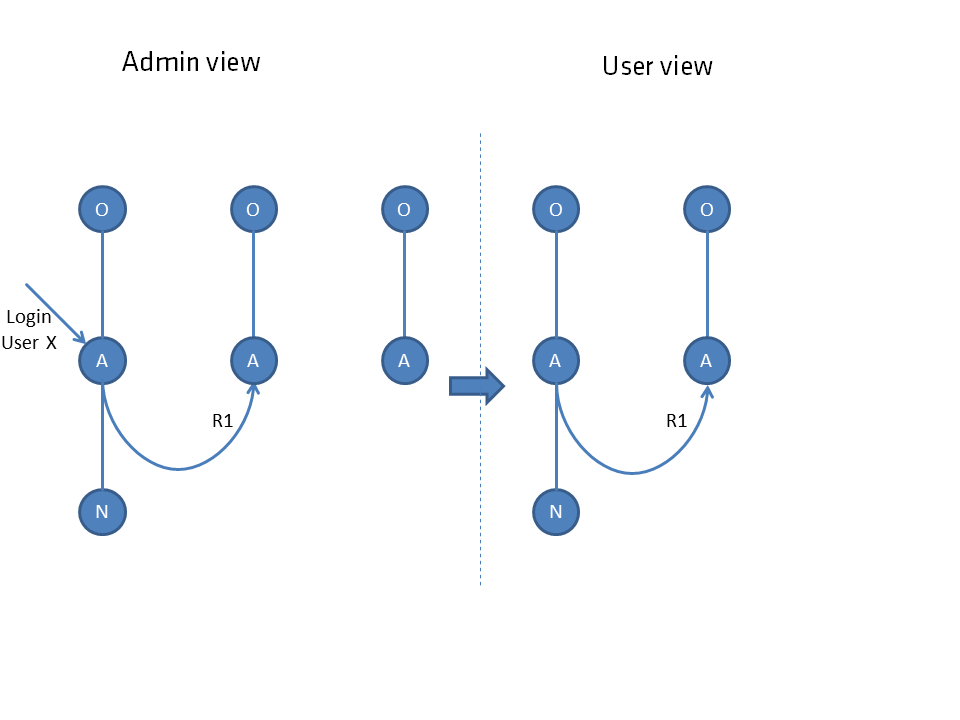 This also applies to chains of any length.
This also applies to chains of any length.
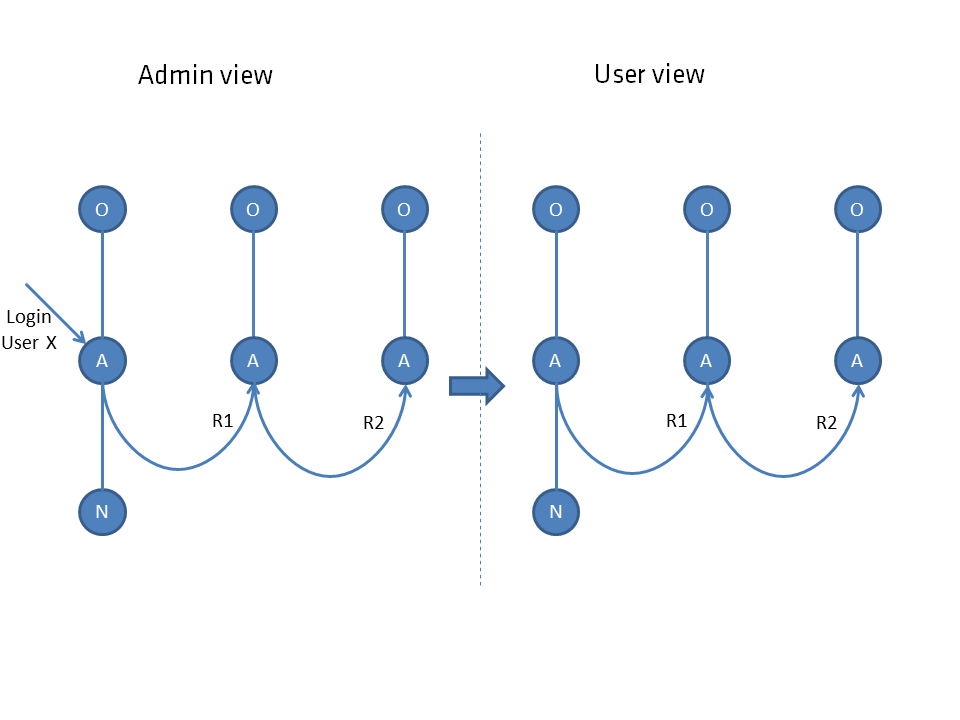 If it does not see the parent node, its node is represented at the parent level.
If it does not see the parent node, its node is represented at the parent level.
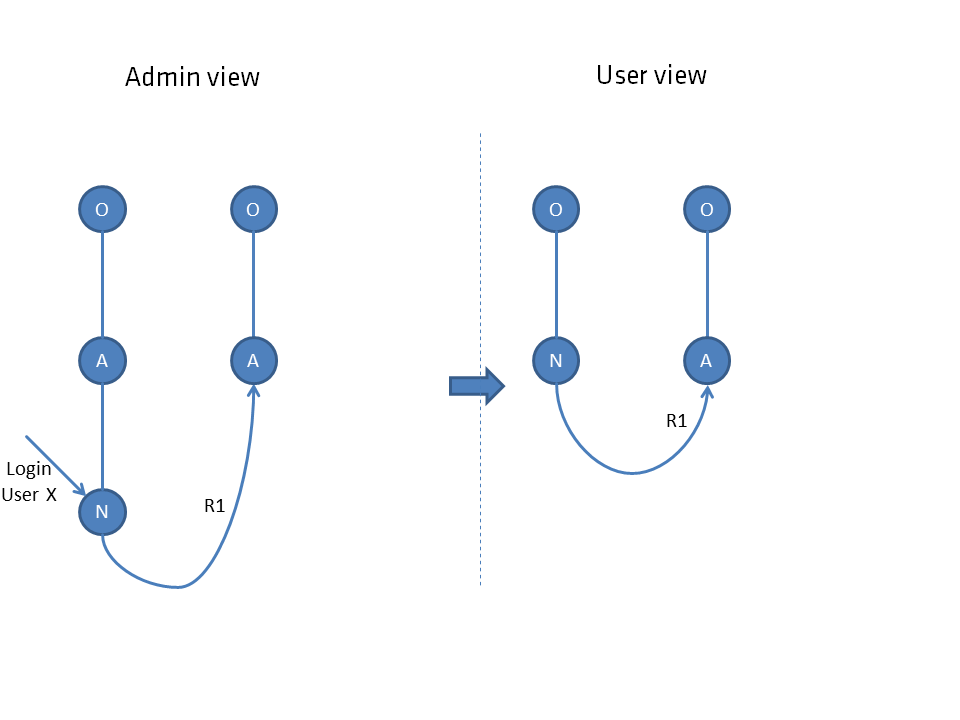
Hybrid forms
If a user does not see a node directly, but indirectly via the parent node, he does not see nodes connected to this child node.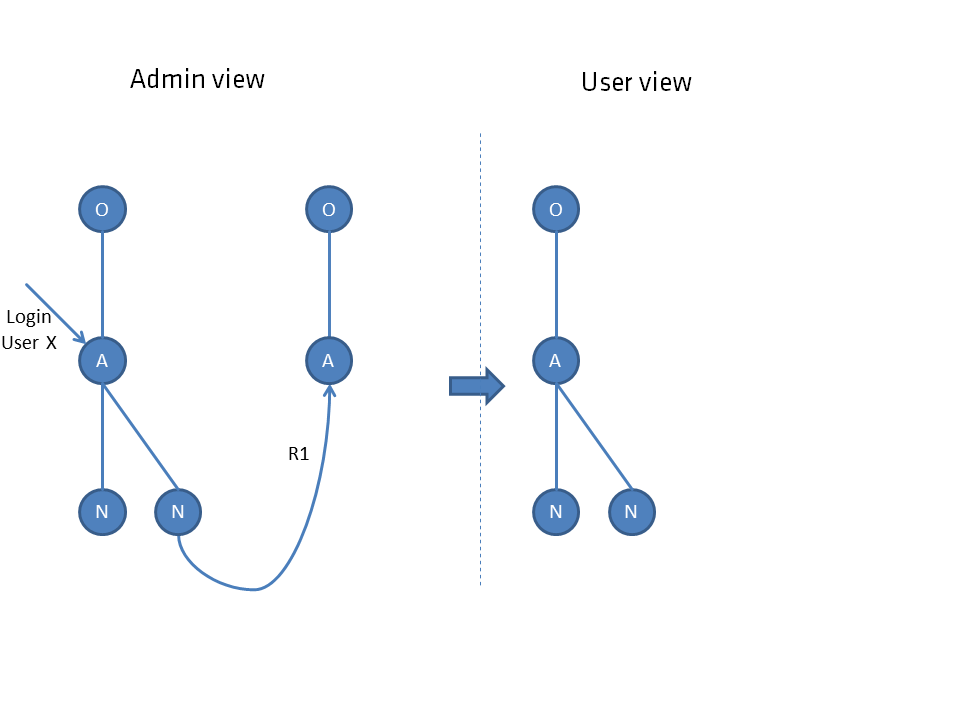 Only directly connected paths are concatenated (R1), indirectly connected paths are ignored (R2).
Only directly connected paths are concatenated (R1), indirectly connected paths are ignored (R2).
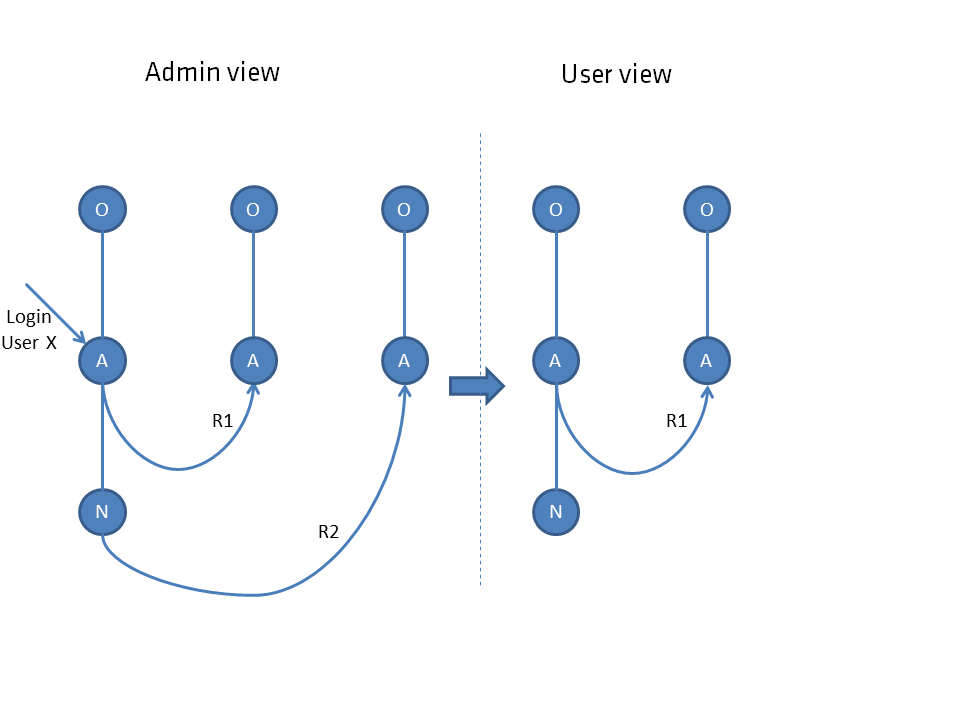 Connections from higher-level nodes also have no effect on the user.
Connections from higher-level nodes also have no effect on the user.
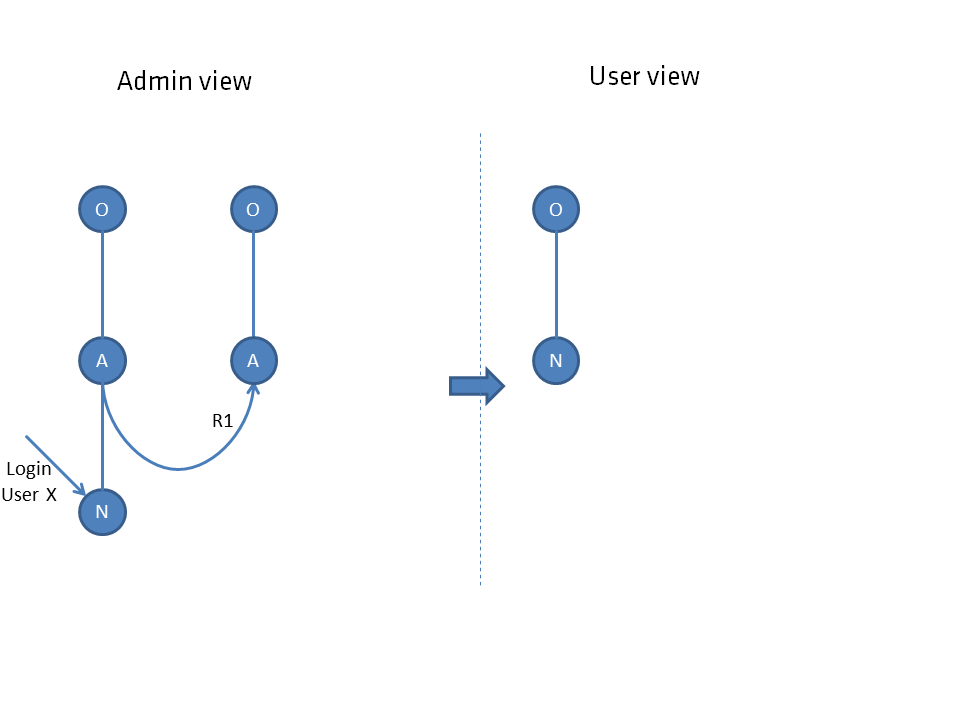 Connections of adjacent aspects are also of no importance as long as no direct connection exists.
Connections of adjacent aspects are also of no importance as long as no direct connection exists.